iOS Backdoors: Apple Denies NSA Affiliation, but the Privacy Is Dead
Backdoors Found in iOS, Apple Says They're Meant for Diagnostics
A lot of fuss is going on around Apple lately, and some of you might get confused at the number of controversy piling up on the news about backdoors in Apple's iOS. Let us see what we know by now first, and then indulge ourselves in some speculations.
A very cool security consultant Jonathan Zdziarski made some of his fundamental research about iOS public. Zdziarski is not only a researcher, he is also a consultant and trainer for the military and governmental institutions on technology and security, helping them solve technically complicated cases in the US, Canada and the UK, among other things. I suggest you visit his blog and give it a thorough read, if you need to make sure for yourself if the specialist is credible. Apparently, the courts here in the US think him credible since he often testifies against criminals as a technical specialist.
Now, the paper he published reveals some highly alarming, and at the same time unsurprising revelations - Identifying Backdoors, Attack Points, and Surveillance Mechanisms in iOS Devices by Jonathan Zdziarski. The backdoors Mr. Zdziarski refers to are meant for Apple's undocumented services, that is such services users were unaware of until now.
Apple reluctantly admits these services exist and are meant for Apple use only, but seriously downplaying the importance of vulnerabilities created by these backdoors.
The main conflict here was created by media, as usual, with the major tech outlets drawing logical conclusions Apple must be working with the NSA. What Mr. Zdziarski basically meant to do by going public with his findings was to let the audience draw their own conclusions. As he explains in his blog:
I have NOT accused Apple of working with NSA, however I suspect (based on released documents) that some of these services MAY have been used by NSA to collect data on potential targets. I am not suggesting some grand conspiracy; there are, however, some services running in iOS that shouldn’t be there, that were intentionally added by Apple as part of the firmware, and that bypass backup encryption while copying more of your personal data than ever should come off the phone for the average consumer.
Apple denies these undocumented services were created under the umbrella of collaboration with the NSA or any other governmental or third-party agency seeking to access users' personal data, and the undocumented services are meant for the diagnostics purposes only.
Zdziarski, on the other hand, says he doesn't 'buy for a minute that these services are intended solely for diagnostics.' The type of data made exposed by the backdoors is 'of an extreme personal nature,' which is way beyond the scope of hardware or software diagnostics needs, as reports mashable.
Now, let us get to the dessert -
Which personal data your device has been and is siphoning through these wide open backdoors?
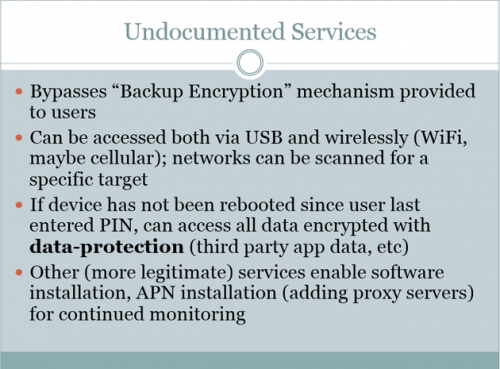
At the Hope X hacker conference, Zdziarski mainly focused on three undocumented services that go by the names of com.apple.pcapd, com.apple.mobile.file_relay and com.apple.mobile.house_arrest. You can access the slides here.
- pcapd is called 'packet sniffer' in hackers jargon, and what it does is records all incoming and outgoing traffic on your iPhone. The service is installed on iOS devices by default, and runs irrespective of whether the device is in the developer mode, or not. It does not warn a user when or if it's running. According to Zdziarski, 'This means anyone with a pairing record can connect to a target device via USB or Wi-Fi and listen in on the target’s network traffic.' According to Zdziarski's March article published in technical journal: "Every desktop that a phone has been plugged into (especially prior to iOS 7) is given a skeleton key to the phone," which can then be copied along with the certificates from one computer to another.
- file_relay service collects large volumes of raw data from iPhones and uploads it in unencrypted form, according to Zdziarski. In iOS 7, file_relay has access to 44 data sources, including the ones dealing specifically with users' personal information: accounts, address book, GPS logs, photos, calendar files, notes, call history, maps of the device's entire file system, voicemail, a hefty collection of all words you ever typed into your device and plenty of data on your personal activity cached in temporary files. Zdziarski refers to file_relay service as the key backdoor and 'the biggest forensic trove of intelligence on a device's owner' providing sensitive information about the person that would only be of interest to 'law enforcement or spying agencies.'
- house_arrest has access to a large spectrum of app-related data - photos, screenshots, databases, cached data. In other words, apps you use, games you play are also completely transparent and can be accessed and assessed by anyone knowing of the backdoors.
Facts and Speculations
1. Apple admits Mr.Zdziarski's findings are accurate.
2. Apple kept the information about the backdoors undisclosed up until now, which means independent researchers could not evaluate objectively how much a threat the backdoors pose.
3. Now that everybody knows about them, Apple releases a statement explaining why they need the 'backdoors' and how the company uses them for diagnostic purposes. Mr. Zdziarski is more than skeptical about the explanation for a good reason.
4. Mr. Zdziarski did not suggest Apple was working with NSA, or any other surveillance agency, when leaving the backdoors in iOS. Instead, he underlined - the backdoors are there; they can be found and exploited by both criminals and governments alike. And since they are there, there are parties exploiting them.
5. At these heights, it does not really matter if Apple and NSA shook hands on this. Backdoors are there for anyone savvy enough to make use of them.
6. Apple does not look good in all this mess, especially since the tech community always used to laugh at Google's 'secure Android,' with iOS always coming out on top as a digital fortress.
7. Conspiracy theorists backed by WikiLeaks and Edward Snowden files receive yet another strong backing in Zdziarski’s findings. They have long ago added tech Goliaths to the list of the notoriously mysterious and sinister Bilderberg Group, something of a Zionist world leaders' club largely ridiculed by mainstream media. Now, they have more facts to operate with when connecting Apple to state surveillance practices.
Is it time to panic?
- Yes, if you think you might be a person of interest for the NSA or the Police, or any governmental agency of your country.
- No, but the privacy is dead and Zdziarski's findings are the last nails in its coffin.
Who Gets to Say the Final Words
There is not much Apple representatives can say here to sound credible and trustworthy, even though it was not Zdziarski's intention to discredit the manufacturer or suggest any conspiracy. He hopes Apple will 'quietly fix most of them,' otherwise it would be highly 'irresponsible' of them now that the public is aware.
I would not focus on Apple-NSA pair in the light of these revelations. Instead, I would put the issue in a global perspective - international corporations, which Apple is, might be the true puppeteers behind NSA, Police or any government for that matter, and not the other way around as we are used to thinking, especially if you think of the total unaccountability of corporations.
Zdziarski published a video on YouTube detailing on what the undocumented services can and can not do, and we suggest you go through it for educational purposes:
Sources: Zdziarski's blog, The Next Web, Ars Technica, Read Write 1, Read Write 2, Zdziarski article in technical journal, Apple support blog, The Inquirer, Mashable.