TrueCrypt Audit Phase 2 Report: 4 Vulnerabilities Found. VeraCrypt Releases An Update
 Last year, we reported on a strange demise of one of the most veritable encryption programs that has been the leader of hard drive encryption since 1998. Created by two men, TrueCrypt was and still is a “a monumental and truly impressive” software that was the source of continuous outrage and irritation to the NSA and the likes of it. However, last years its users found a disturbing message on the project's website, saying that the latest 7.1a version was not safe, the project was abandoned by its creators and the users should find a replacement. Shortly before that, an Open Crypto Audit Project to independently audit TrueCrypt's source code was initiated by Matthew Green and Kenneth White.
Last year, we reported on a strange demise of one of the most veritable encryption programs that has been the leader of hard drive encryption since 1998. Created by two men, TrueCrypt was and still is a “a monumental and truly impressive” software that was the source of continuous outrage and irritation to the NSA and the likes of it. However, last years its users found a disturbing message on the project's website, saying that the latest 7.1a version was not safe, the project was abandoned by its creators and the users should find a replacement. Shortly before that, an Open Crypto Audit Project to independently audit TrueCrypt's source code was initiated by Matthew Green and Kenneth White.
TC was under the audit for about a year, and we published the results of the first audit part, which stated that the encryption specialists did not find any backdoors in the code. In April 2015, the second and final part of the audit was completed, and the official website for the effort published a short pdf summarizing the team's findings.
Conducted by three security engineers, Alex Balducci, Sean Devlin and Tom Ritter, the audit covered not the full scope of TC's code, but the most crucial parts of it. According to the final report, no evidence of backdoors deliberately left by the TC creators were found. Neither is there any severe flaws in the code's design that could make the program vulnerable in most cases.
4 Vulnerabilities Found
TrueCrypt is not without flaws, however, and the report states four vulnerabilities were found. Some are there due to incautious coding, others are glitches that, under some very specific circumstances, may make TC less bullet-proof than its users would like it.
The four found vulnerabilities are as follows:
- CryptAcquireContext may silently fail in unusual scenarios - high severity
- AES implementation susceptible to cache timing attacks - high severity
- Keyfile mixing is not cryptographically sound - low severity
- Unauthenticated ciphertext in volume headers – undetermined
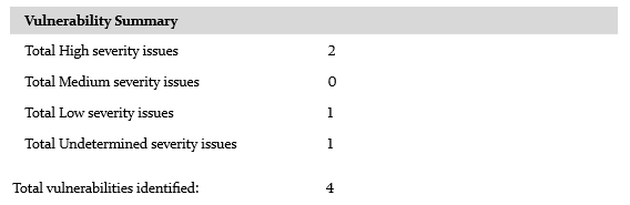 Image: Open Crypto Audit, part II
Image: Open Crypto Audit, part II
The most significant vulnerability, the CryptAcquireContext, is related to TC relying on Windows random number generator, RNG, among other things, to generate the keys that TC uses to encrypt its volumes. The RNG implemented in TrueCrypt takes its roots in 1998, when the developer first created an entropy pool to mine for unpredictable values from a variety of different sources, as explains Matthew Green in his blog.
If you remember how the TC guide asked you to move your mouse as randomly as possible when generating the keys, that is one such source of unpredictable values for the TC's entropy pool. Windows API is one of these sources, and in rare cases, but very rare, it can fail to start properly, in which case TC should not accept the values. Well, it does accept them, and should this rare case happen someone would end up with a key that compromises the system or volume. It is quite a significant cause for concern since a predictable number generator is no longer random and can compromise security of the entire system.
At the same time, TrueCrypt collects entropy from other sources, like the mouse movements and other random system pointers, so the likelihood of TC getting a predictable key is very low.
Also, cache timing attacks may result efficient against TC's AES code, the report notes, which should only be of concern to those who have their TC encrypted files on a shared device or in a sandbox or browser.
Image: Open Crypto Audit, part II
The Forks
Nonetheless, the report suggests anyone working on a fork of TrueCrypt should take into account the discovered flaw and fix it in their fork.
VeraCrypt and CipherShed are the two forks of TrueCrypt, with VeraCrypt being the one that seems to receive frequent updates at least. Based on the audit report, Idrix, the company behind VeraCrypt released an update, VeraCrypt 1.0f-2, patching the CryptAcquireContext vulnerability found in TC source code. The other three vulnerabilities haven't been addressed in the latest update, however, but since they may present a threat only under very peculiar circumstances, they are of less concern. Nonetheless, if an attacker should have access to the victim's computer, they still might be exploited. The developers of VeraCrypt assure they are working on a patch for the cache-timing attacks and the keyfile generation vulnerabilities, and they plan to release the next update within the next couple of weeks:
Cache-timing attacks are realistic on multi-user server environment where a malicious user can recover sensitive keys from the CPU. This type of shared environment is clearly not recommended for TrueCrypt/VeraCrypt because of other security risks so this is not a realistic scenario in our context.
<...> Anyway, since this applies to all cryptographic libraries, we should seek external help/advice from other open source projects to look for available general purpose implementations that brings some level of protection without loosing too much performance. <...> The last point concerning unauthenticated plain text in the decrypted header is not a realistic attack at all.
VeraCrypt's functionality has been widened, too. Until now it only worked with TrueCrypt volumes, not partitions, which has been addressed, and now the program supports the mounting of TC system partitions. Other minor changes have been introduced, too.
Nonetheless, ArsTechnica suggests there may be complications with the TrueCrypt forks, since the license explicitly forbids forking TC. Whether or not the largely anonymous developers of the original TrueCrypt would want to pursue legal action against the developers of the TC forks is not clear for the moment. What is clear the creators of TC have obviously jumped ship, and some users even named TrueCrypt as “abandonware.”
Finally, the number of users still sticking to the latest TrueCrypt version seems to be quite large, at least according to the comments on public forums, where users suggest there is nothing inherently wrong or malicious with the program.
Tin foil hatters suggest NSA knows it all about you anyway while the events surrounding the TC demise are so vague and mysterious, we would suggest Lara Poitras and Glenn Greenwald make an investigation about that. Especially since the NSA whistleblower Edward Snowden endorsed TrueCrypt, bringing the non-initiated public attention to the powerful encryption tool.

