Android SMS worm Selfmite Returns and Is More Scary Than Before
The Selfmite SMS Worm that previously affected mobile devices using the Android OS has come roaring back with a vengeance in a second selfmite.b version which is 100 times more communicative.
The trojan is accessed by users who click on a malicious web link which then downloads and installs a Android APK package which reads the address book and begins sending out infectious SMS messages of its own to the first 20 entries in an address book. The worm has so far spread to at least 16 countries sending spam text messages. Over 150,000 SMS messages have been sent in just the first 10 days since security firms became away of the Selfmite.b variant threat.
How The Selfmite.b Trojan Works
The first 20 contacts in an address book are sent an SMS text message with a link to a rogue download package. The trojan will run through the first 20 contacts and then loop back to the first and continue sending SMS text messages in an endless loop until cellular credit runs out. For anyone not on an unlimited SMS texting package the financial costs can be considerable. An estimated 1,500 SMS texts are send for every Android device that becomes infected.
The infectious links point to a url shortening site that was hosted by GoDaddy until they were advised and shutdown the hosting. However, with the selfmite.b variant the malicious links to the infectious Android APK can be changed remotely by the creator as they are not hard coded into the trojan like they were with the selfmite.a version. So the threat remains present.
 Avoiding Becoming Infected By Selfmite.b
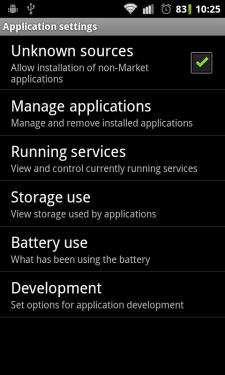
Avoiding Becoming Infected By Selfmite.b
The distribution of this trojan relies on the Android OS accepting the installation of third party apps from an untrusted source. By default Google Android OS is set to not accept app installations from unknown sources. See the accompanying capture for more information.
Check whether your device is set up securely to avoid possible infection later:
Settings > Applications > Unknown sources
How To Know If You've Been Infected
Is your cell phone credit disappearing fast and you cannot figure out how or why? This could be the reason.
The infectious APK file installs two apps to the home screen of the Android device. The first is Mobogenie and the second is Mobo Market. These are just web links and when clicking on them they can open other apps or go online to access web pages. The behavior changes depending on the IP address of the Android device owner. Have a look at your home screen to see if there are any such apps that you haven't installed. But do not click on them.
Avoid clicking any links contained in SMS text messages even from friends and colleagues. Contact them separately to check what the link relates to in order to ensure that they actually deliberately sent it to you and it's not a message generated by a trojan infection on their Android device.
Removal Options
Symantec have been looking into the risks of the Selfmite trojan for some time. They offer a Norton Mobile Security package which can detect and remove the Seflmite.b infection from an Android device. The Norton Mobile Security app is available for free use for 90 days before needing to purchase a subscription.
