Latest articles tagged “security”
Yahoo fields 18,594 government requests for data in first 6 months of 2014
by Pete Daniel
on 26 September 2014
·
1562 views
In a continuation of their global transparency reporting, Yahoo has revealed that they received 18,594 US government information requests for 30,551 accounts from January–June 2014. This is the third global transparency report Yahoo has published. ... Read more
TunnelBear VPN Updated for iOS and Android
by Pete Daniel
on 26 September 2014
·
2879 views
TunnelBear, the virtual private network (VPN) app for iOS, Android, Windows and the Mac, has been updated for their Android and iOS version. Gone is the darker graphics and in comes a more attractive colorful look. ... Read more
1.4 million customers affected by data breach in TripAdvisor's Viator
by Gary Oldwood
on 25 September 2014
·
4286 views
Viator (TripAdvisor’s website for tour-booking and reviews) is the recent victim of a data breach that resulted in the loss of data from 1.4 million customers, including email addresses, passwords, Viator nicknames and payment card data. ... Read more
New 'Stripe' Payment Processing Startup Partners with Apple and Twitter
by Chris Thomas
on 25 September 2014
·
1986 views
The relatively new payment processing startup 'Stripe' is off to a very successful start, as it has already developed partnerships with major companies like Apple, Twitter, Lyft, and Shopify. ... Read more
Reports Surface of Almost 5 million Gmail Accounts With Passwords Exposed
by Pete Daniel
on 12 September 2014
·
2797 views
Reports have surfaced that hackers located in Russian have managed to obtain crucial information in order to allow the infiltration of up to 4.93 million Google accounts. This includes the email IDs and selected passwords to access Gmail, etc. ... Read more
Viber Goes Video on Mobile Platforms, Finally
by Pete Daniel
on 12 September 2014
·
2832 views
Viber is expanding into mobile-based video calling. Video calling is nothing new for desktop users of Viber on Windows PCs and Macs. The mobile versions have undergone two years of experimental testing on iOS and Android in order to get it right. ... Read more
Fake Cell Towers Across USA Tracking Users
by Pete Daniel
on 11 September 2014
·
2485 views
Just when you thought you were safe with your Android phone, it has now been learned that authorities across the USA including some law enforcement agencies are using a secondary cell tower to capture unencrypted phone calls. ... Read more
Intel’s New Mobile Chips Will Be Always Listening
by Dan Vlasic
on 9 September 2014
·
2006 views
Laptops and tablets powered by Intel chips that hit the shelves later this year will be always listening, be it a good or a bad thing. Enhanced speech recognition can bring the future a tad closer and change how we interact with technology. ... Read more
Windows XP Unofficial Service Pack 4 Available for Download
by Dan Vlasic
on 6 September 2014
·
35990 views
Still on Win XP, but saddened because Microsoft pulled the plug on its most successful product? Rejoice because now you can get your hands on an Unofficial Service Pack 4 from harkaz. ... Read more
Vulnerability in iOS apps can allow attackers to initiate calls from your iPhone
by Gary Oldwood
on 5 September 2014
·
2900 views
A new vulnerability was discovered in Apple’s iOS recently by a developer that allows expensive phone calls to be made from your iPhone without your permission. ... Read more
J. P. Morgan Hack Rumors, Facts and How to Mind Your Personal Banking Cybersecurity
by Dan Vlasic
on 4 September 2014
·
2149 views
large amounts of personal data on customers has been leaked within the past few months - account numbers, personal and financial information of account holders on a large scale. Remember last Christmas Target major hack? ... Read more
Apple Investigating Potential iCloud Flaw That Opened Door To Extensive Celebrity Photo Hack
by Pete Daniel
on 2 September 2014
·
4068 views
The iCloud accounts of numerous A-list and C-list celebrities in the USA and the UK were breached by hackers and photos released on the Internet over the last couple of days. What could be behind the breach in security & how can these be prevented? ... Read more
Why Passive Location Tracking in iOS Is Possibly Bad & How To Disable It
by Pete Daniel
on 2 September 2014
·
2766 views
It may surprise you to learn that your app developers can track your movements even when their app is closed on an iOS-based device. Essentially the features of iOS allow for apps to technically be closed but yet parts of them remain running. ... Read more
How to use the Family Web Filter in Windows 8/8.1
by Michael Black
on 27 August 2014
·
3298 views
The Parental Controls have been replaced by "Family Safety" in both Windows 8 and Windows 8.1. Although the primary concept of keeping your kids safe while using the PC hasn't changed, a few of the mechanics and processes are different. ... Read more
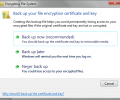
How to Encrypt Files and Folders in Windows 7 and 8/8.1
by Michael Black
on 27 August 2014
·
3182 views
An encrypted file or folder can only be accessed by the user who originally encrypted the file or folder in question. Because of this, encryption has become a great way to prevent unwanted access to sensitive data at the office and at home. ... Read more
Stay Connected
Follow us to get the latest tech tutorials, news, and giveaways as soon as we post them.
Have a Tech Question or News Tip?
Featured Articles
Popular This Week
#news
#windows
#android
#games
#ios
#how tos
#review
#best apps
#security
#google
#windows 10
#free
#microsoft
#apple
#windows 8
#apps
#chrome
#pc
#best games
#mac
#ps4
#smartphone
#answers
#iphone
#samsung
#facebook
#update
#firefox
#xbox one
#xbox